Document Integrity
From version 5.20, the hash value of the assigned document files will be automatically saved to each document.
To ensure document integrity, you can make use of various functions that compare the stored and current hash values. This comparison may provide evidence of problems with storage media and also detect unauthorized access to files:
- The automatic action 'Hash check' checks all document files in the WORK directory of the connected server or on archive media.
- The 'Hash check on object level' automatic action checks all those document files that are specified in a query file.
- Hash values can be compared every time enaio® client requests a document.
- Hash values can be compared before an audit-proof archiving process is started.
- Users with the 'Open properties' system role for individual documents can run an integrity test on object information in enaio® client.
The hash value can also be signed by enaio® server. This largely ensures that unauthorized access to files cannot be concealed by tampering the hash values in the database.
The check results will be logged.
The user will be notified if a hash check, which is performed before enaio® client opens a document, has determined that the hash values are different. In such cases, only users with the 'DMS: Supervisor' system role are enabled to open these documents in read-only mode.
When carrying out the check before archiving, the corresponding documents are not archived if the hash values do not match.
Regardless of the document integrity checks, hash values are identified before and after every document transfer to eliminate transmission errors.
Hash Value and Hash Value Signature
From version 5.20, a hash value is automatically generated and saved to the database whenever a document containing pages is created or edited.
The feature which signs hash values is activated in enaio® enterprise-manager:
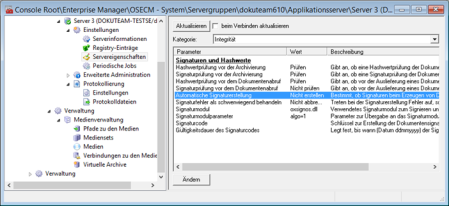
Open the Server properties > Category: Integrity area and double-click the Automatic signature creation parameter to set its value to Create.
As a result, the hash values generated during archiving as well as when document files are created and edited will be signed by enaio® server.
The two parameters Signature module and Signature module parameters are set automatically. Change these entries only if explicitly instructed to do so by our consulting team.
The Signature errors treated as severe parameter specifies whether or not to cancel the corresponding action in case of errors while signatures are being checked or created.
Errors could include, for example, failed communication with a signature module or a trust center and errors caused by expired certificates.
Do not cancel is set by default.
Subsequently Creating Hash Values
Hash checks can only be effectively used if hash values for all document files exist. Hash values are also necessary in order to carry out checks for identical documents while new ones are being created (see 'Checking for Identical Documents').
Use the 'Sign' automatic action to generate signed or unsigned hash values for document files that were created in software versions earlier than 5.20, and sign existing hash values.
Note that this action will take significant time and require considerable resources if it is carried out on a very large pool of documents. This is why you need to plan this action carefully. To test in advance how long it will take to complete the action, use a small number of representative documents. Also keep in mind that the Maximum number of hits setting in enaio® enterprise-manager limits the number of documents that can be processed. If more than 50,000 documents are to be signed, this setting must be changed.
If you want to perform the automatic action, you need a password and a signature code. Both have a limited period of validity. If you only want to create hash values afterwards, you also need both of them.
This data will be provided by our consulting team at your request. We will require your current license file to create this data.
Before configuring the automatic action 'Sign', switch to enaio® enterprise-manager and enter the signature code and the period of validity:
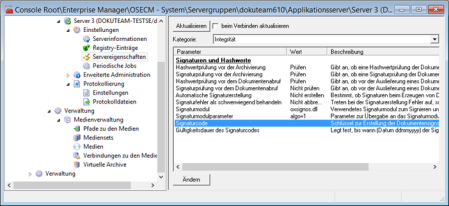
You will find the Signature code and Period of validity parameters in the Server properties > Category: Integrity area. Enter the appropriate values there.
After the period of validity has expired, the 'Sign' action can no longer be carried out.
To use the 'Sign' automatic action, add the axacsign.dll library to the Entire system> Additions tab in enaio® administrator (see ''Additions' Tab'). You can then create configurations for the action and execute it manually using enaio® administrator or at a scheduled time using enaio® start (see 'Setting Up Automatic Actions').
Configuring the 'Sign' Action
The signature code and period of validity for the 'Sign' action are specified in enaio® enterprise-manager; the required password must be entered in a configuration dialog.
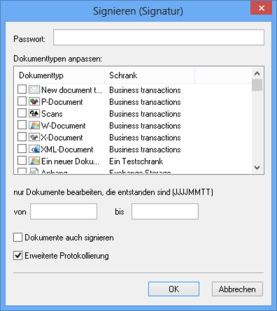
Hash values will be generated for all documents of the document types you have selected here. As an additional criterion, you can specify a timeframe of creation.
If you want to sign the hash values, select the Also sign documents option.
The action logs according to the settings in the oxrpt.cfg configuration file in the application directory. Additionally, a log file named axacsign_date_time.xml is created in the configured log directory. Errors are logged there. Select the Advanced logging option to have detailed information written to this file.
This action always creates new hash values, even if there are previously generated hash values. These hash values are not compared. For security reasons, carry out a hash check when generating documents for which hash values already exist.
The 'Hash Check' Automatic Actions
Two automatic actions for hash value and signature check are available:
- the 'Hash check' action – axachash.dll
Select either archiving media or the WORK directory for checking.
- the 'Hash check at object level' action – axachashd.dll
You will need to create a query file in which you can enter precise criteria for the hash check.
To use the automatic actions, add them in enaio® administrator on the Entire system > Additions tab (see ''Additions' Tab'). You can then create configurations for the actions and execute them manually using enaio® administrator or at a scheduled time using enaio® start (see 'Setting Up Automatic Actions').
Keep in mind that the Maximum number of hits setting in enaio® enterprise-manager limits the number of documents that can be processed. If more than 50,000 documents are to be checked, this setting must be changed.
Hash Check
Specify the archive medium to be tested or the WORK directory of the connected server for the 'Hash check' action. In the case of archive media, mirrored media for a main medium are also checked automatically.
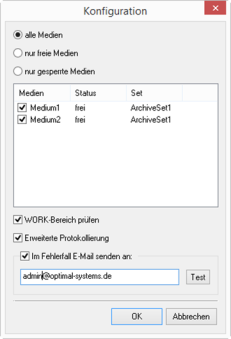
The action logs according to the settings in the oxrpt.cfg configuration file in the application directory. Additionally, a log file named axachash_date_time.xml is created in the configured log directory. Errors are logged there. Select the Advanced logging option to have detailed information written to this file.
You can specify an e-mail address for a message to be sent in the event of an error.
Hash Check on the Object Level
You will need to create a query file for the 'Hash check on object level' action. Specify this query file during configuration.
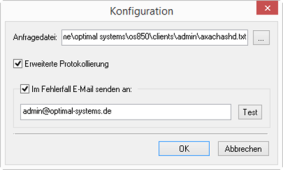
The action logs according to the settings in the oxrpt.cfg configuration file in the application directory. Additionally, a log file named axachashd_date_time.xml is created in the configured log directory. Errors are logged there. Select the Advanced logging option to have detailed information written to this file.
You can specify an e-mail address for a message to be sent in the event of an error.
Query File
You can create the query file with any text editor. It has the following structure:
| [QUERY] |
The file begins with the 'query' section. |
| SCHRANK=folder type name |
Enter the name of the folder type that the objects originate from into the first line. |
| REGISTER=register name |
Optionally, you can enter the name of the register from the objects originate. |
| DOCUMENT=document type name |
Enter the name of the document type from which the objects originate. |
| CLAUSE1=Object@Field=Value CLAUSE=Object@Field=Value |
Optional clauses allow you to limit the selection to those objects that fulfill these conditions. Clauses must be numbered consecutively. |
| EXPRESSION1=object@field^operator^value ... EXPRESSIONn=object@field^operator^vaue |
Optional clauses allow you to limit the selection to those objects that correspond to these expressions. The expressions must be numbered consecutively. |
If you use internal names, enclose the name in percent signs.
Clauses
Optional clauses allow you to limit the selection to those objects that are indexed with the entered value in the specified field.
Example:
CLAUSE1=Customer@Status=completedDocuments of the specified document type are checked using the document query only if the index data of the DMS object type 'Customer', e.g., a folder, contains the value 'completed' in the 'Status' field.
Detailed information on query files can be found in the enaio® client - Programming Reference.
Expressions
Expressions allow you to limit the selection to objects by specifying technical parameters, e.g., basic parameters containing values.
Example:
Expression1=Contract@1102^2^8Only documents of the document type 'Contract' which do not contain the value '8' in the field for the archiving status '1102' will be checked.
Documents without pages have the archiving status '8'.
The 'Hash check at object level' action logs errors when checking documents without pages. It is therefore recommended that you use an expression to prevent these documents from being checked.
Continual Hash Check
You are only allowed to turn on continual hash checks if you have ensured that a hash value is present for every document file, whereas continual signature checks additionally require that all hash values have been signed and that automatic signing has been activated.
You can configure enaio® server to check the hash value every time a document is retrieved. If the newly-generated hash value fails to match the saved value, the user is notified in enaio® client and the document is not opened.
Only users with the 'DMS: Supervisor' system role are enabled to open such documents in read-only mode, provided that they are legible at all. The file can be saved externally, for example, but the document cannot be recovered.
You can define whether hash values match or not; if they do not match, however, you cannot identify the reason.
Continual hash check can be activated in enaio® enterprise-manager.
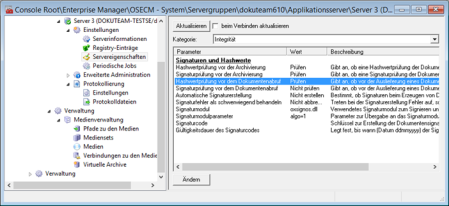
Open the Server properties > Category: Integrity area and double-click the Hash check before document request parameter to set its value to Check.
If the hash values are signed, you can additionally activate the Signature check before document request.
The Signature errors treated as severe parameter specifies whether or not to cancel the corresponding action in case of errors while signatures are being checked or created.
Errors could include, for example, failed communication with a signature module or a trust center and errors caused by expired certificates.
Do not cancel is set by default.
Hash Check Before Archiving
You are only allowed to turn on hash checks if you have ensured that a hash value is present for every relevant document file, whereas continual signature checks prior to archiving only require that all hash values have been signed.
enaio® server can run a hash check before documents are archived. If the newly-generated hash value fails to match the saved value, the document will not be archived.
Hash check before archiving is activated in enaio® enterprise-manager.
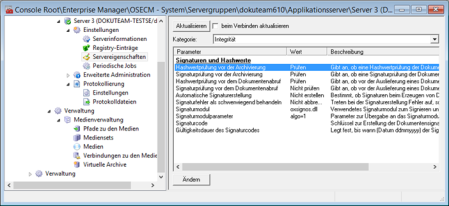
Open the Server properties > Category: Integrity area and double-click the Hash check before archiving parameter to set its value to Check.
If the hash values are signed, you can additionally activate Signature check before archiving.
The Signature errors treated as severe parameter specifies whether or not to cancel the corresponding action in case of errors while signatures are being checked or created. Errors could include, for example, failed communication with a signature module or a trust center and errors caused by expired certificates.
Do not cancel is set by default.
 areas. Use the toolbar to show all hidden areas at once:
areas. Use the toolbar to show all hidden areas at once:
