Third-Party Components
Last update: Dec 22, 2021, 1:20 PM CET
As part of the risk analysis, we additionally collect announcements from our partners and software vendors whose 3rd party products we have used in our customer projects on a project-specific basis. Therefore, we would like to draw your attention here to such components where the affected Java libraries were also used. This page contains information about third-party products that we know are affected by this vulnerability. For products that are not listed here, visit the websites of the respective developers for the latest information.
Please check the following project-specific components and adjust the environment variables if necessary:
Datev Bridge by RIB Leipzig GmbH (formerly known as DATENGUT Leipzig GmbH & Co. KG)
also known under the module names enaio® DATEVBridge, enaio® datev-bridge, enaio® Datevconnect, enaio® Datenleser, DATEV Schnittstelle
Please contact your project representative to schedule any additional updates that may be provided. We strongly recommend to update the affected Java libraries. As an interim solution, the Java parameter -Dlog4j2.formatMsgNoLookups=true can be set.
Our project partner RIB Leipzig GmbH gives the following recommendation:
Under certain conditions, the application iTWOsite is affected by the critical Zero Day Exploit in Log4j. We have been working on a patch for the application since Friday. An update of this component is strongly recommended, as soon as we release the patch.
Until then, it is necessary to apply a workaround to the application, so that the vulnerability cannot be exploited.
Please carry out the following adjustments as soon as possible and inform your project representative at RIB. It is possible that some adjustments have already been carried out. Please contact your representative directly for more information.
Affected application: Tomcat („Webclient“ / “Storage“ / “DLWeb“)
The following Java parameter must be set in all Tomcats of the application (Webserver + Storage Server are affected (possibly on the same machine):
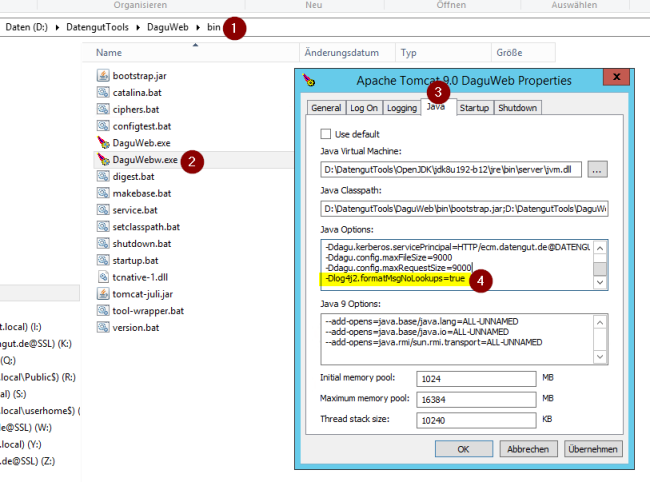
-Dlog4j2.formatMsgNoLookups=true
Please refer to the screenshot below (the line break under the parameter at the very bottom must be preserved).
For each Tomcat installation navigate to the bin directory.
Open the Tomcat configuration.
Switch to the Java tab.
Enter the parameter in the Java Options: area (Note: the line break must be preserved).
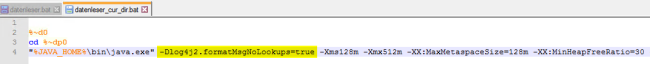
Affected application: „Datenleser“
Adjust the start parameters in the following files: datenleser.bat and datenleser_cur_dir.bat
These are located in the application's root directory.
-Dlog4j2.formatMsgNoLookups=true
CloudConnector is not affected.
In addition, the parameter should be set as environment parameter and distributed in the domain via GPO. Other applications are not affected for the time being.
Set environment variable LOG4J_FORMAT_MSG_NO_LOOKUPS to true.
 areas. Use the toolbar to show all hidden areas at once:
areas. Use the toolbar to show all hidden areas at once:
